An unverified contract lost about $140k in several tx. This is a staking contract. There are “stake”, “unstake” functions and also a function for swap tokens.
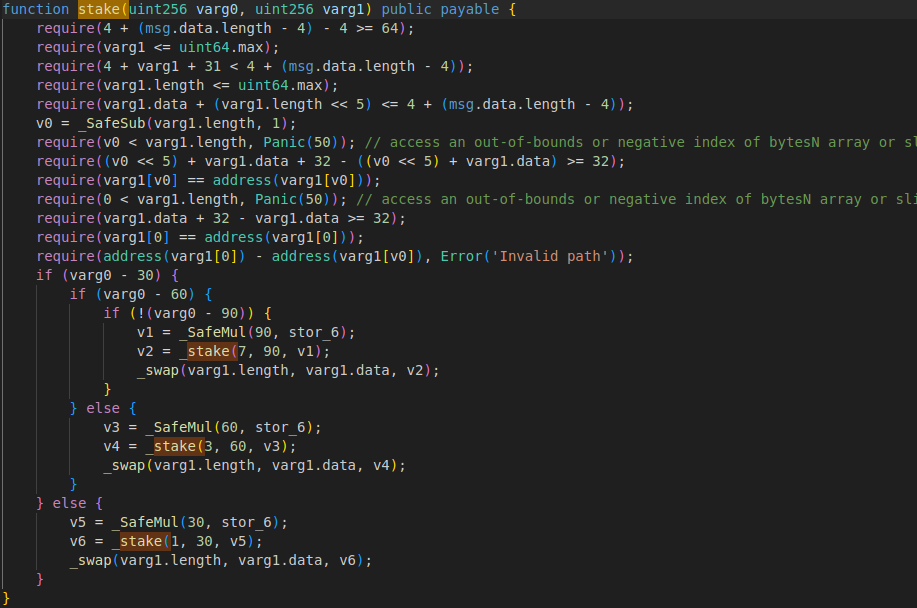
“stake” function stakes usdt token and call “_swap” function. “_swap” function exchanges 10 usdt to other tokens and adds reward according to swap result.
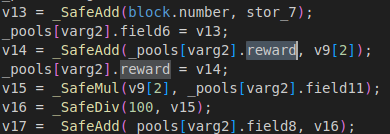
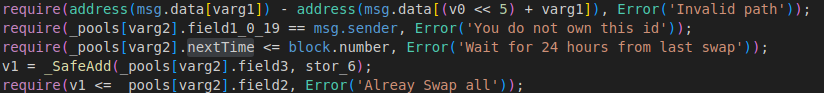
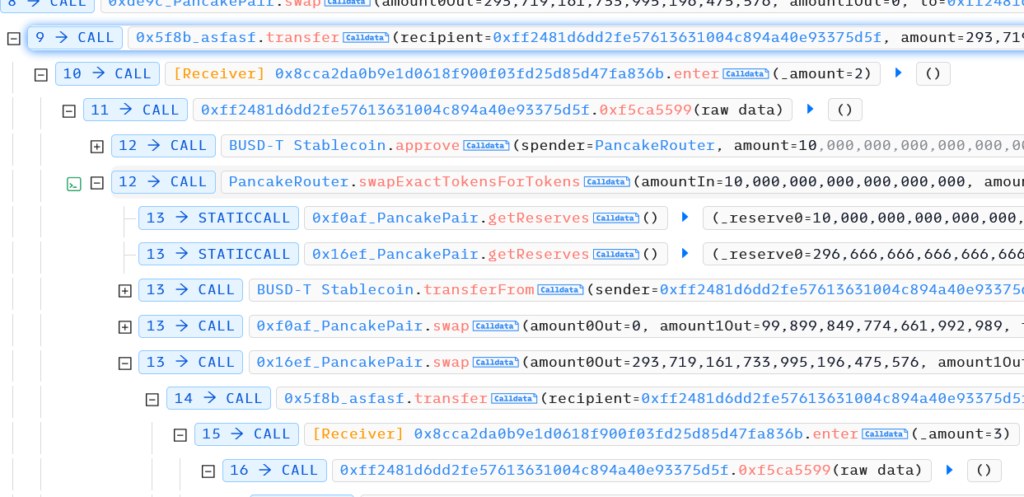
But “_swap” can be called once a day. To evade this, hacker exploited reentrance.
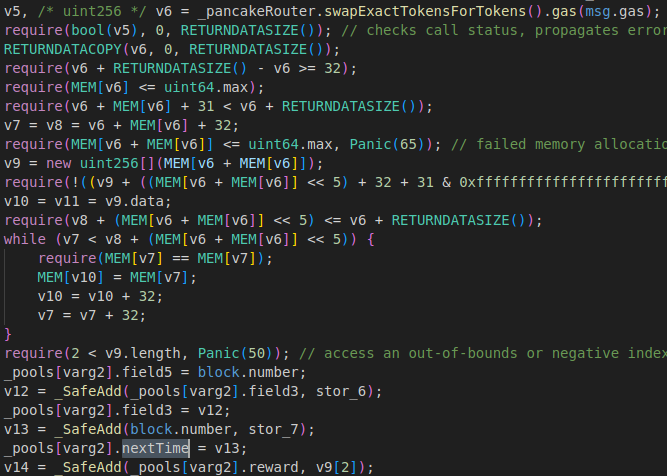
As you can see in photo, nextTime is set after swap tokens. Hacker prepared a token(0x5f8b14fb6cc6008528e461e8073727c38a6a5bf3) that calls “enter” function of attack contract in “transfer” function. Using this token, hacker was able to perform reentrancy attack. 30 times reenter.
Leave a Reply