Onyx protocol was hacked because of improper parameter check.
Vulnerability is in helper contract for Onyx liquidation – NFTLiquidation.
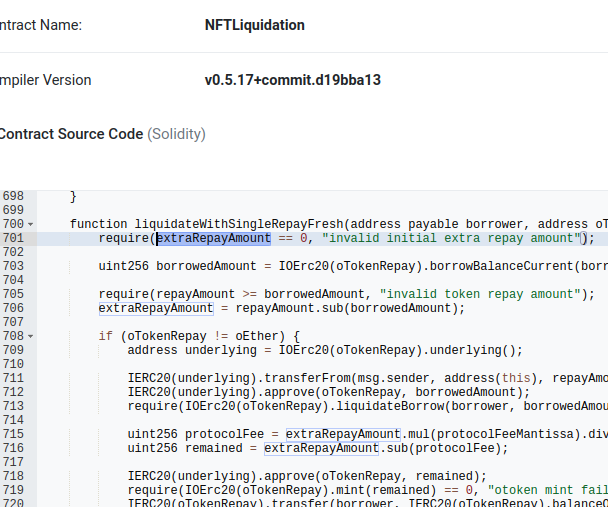
As you can see, there’s “liquidateWithSingleRepay” function. This function is useful when repay amount is larger than borrow amount, it calculates “extraRepayAmount” and use this value to mint new oTokens.
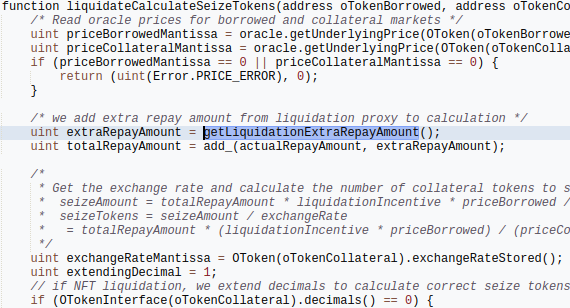
This “extraRepayAmount” is also used in calculation of seize token amount. So far so good.
But what if someone can manipulate this “extraRepayAmount”?
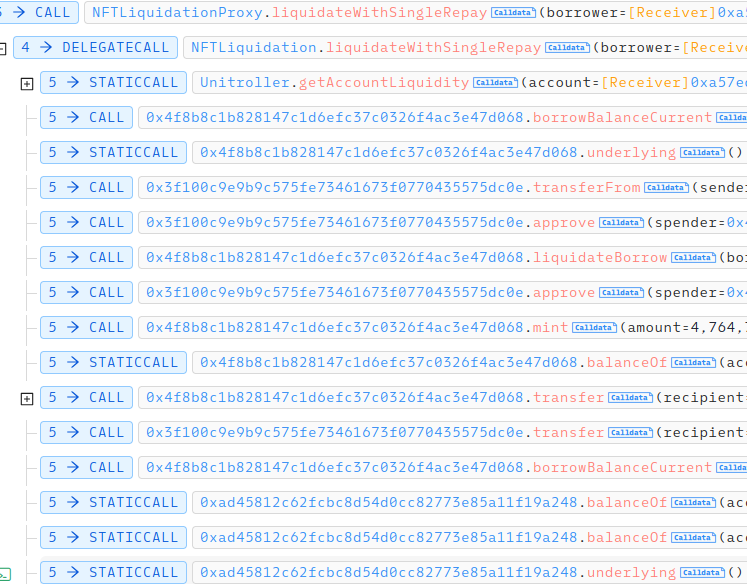
As you can see from picture, strange contracts(not oTokens) are used in liquidation process. These contracts are made just before attack.
Repay amount is 4764735291322, borrow amount is 0, extraRepayAmount is 4764735291322, but no tokens are transferred.
In “transfer” function, real liquidation is called.
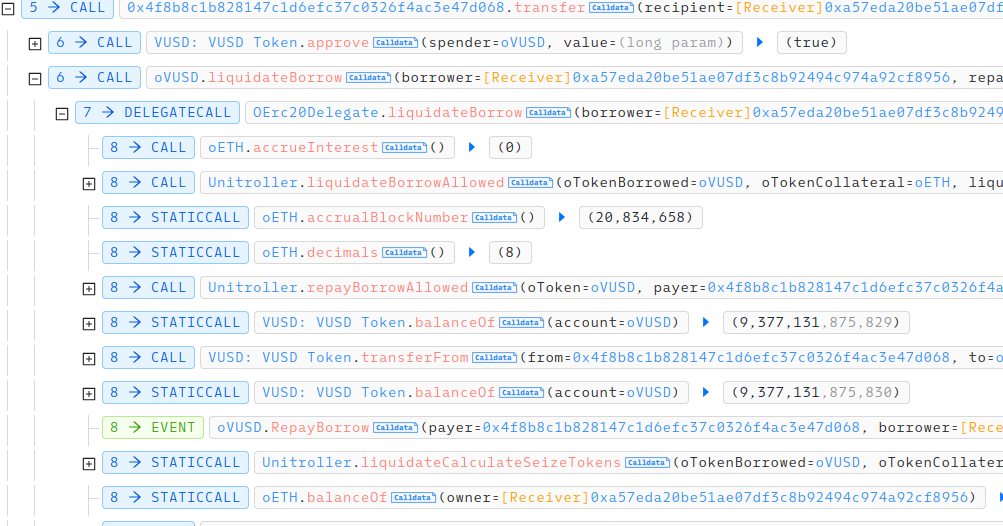
As said before, when calculating seize token amount, extraRepayAmount is used, real repay amount is only 1 wei, but seize token amount is much larger because of this extraRepayAmount.
Whole attack step is following.
Hacker flashloan a large amount of eth, and minted oEth, used it as collateral. Then he borrowed several tokens – DAI, WBTC, USDT, VUSD, XCN.
For liquidation, he had to manipulate exchange rate of oEth. He donated a few Eth into oEth, redeemed a few Eth, repeated this step several times.
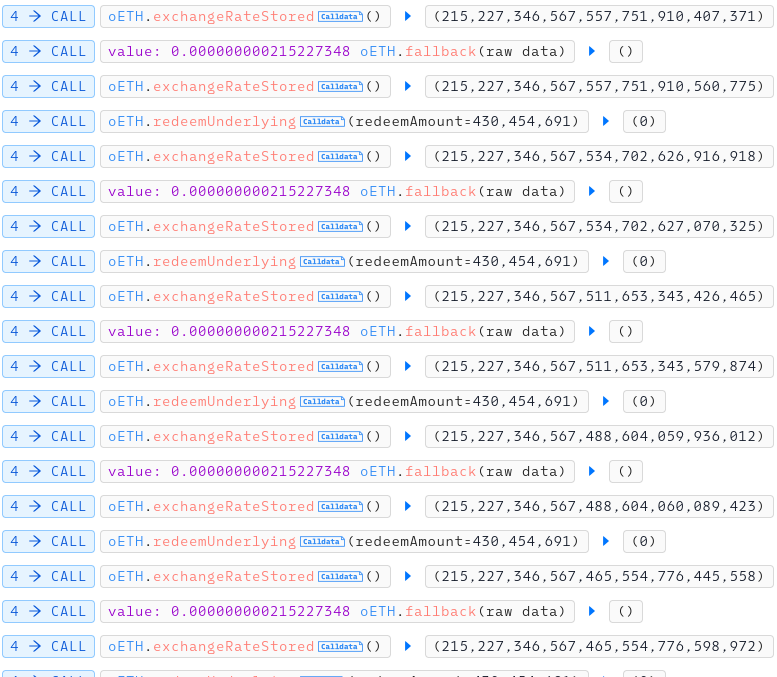
As you can see in picture, exchange rate is getting smaller and smaller.
After exchange rate became small emough, he was able to liquidate borrow position. He used above vulnerability, using only 1 wei of VUSD, he could get almost all collateral eth. He gained about $4m.
There should be parameter check in NFTLiquidation contract. It should check if inputed oTokens are listed in Comptroller.
Leave a Reply