Vestra DAO staking contract exploited because of wrong unstake logic.
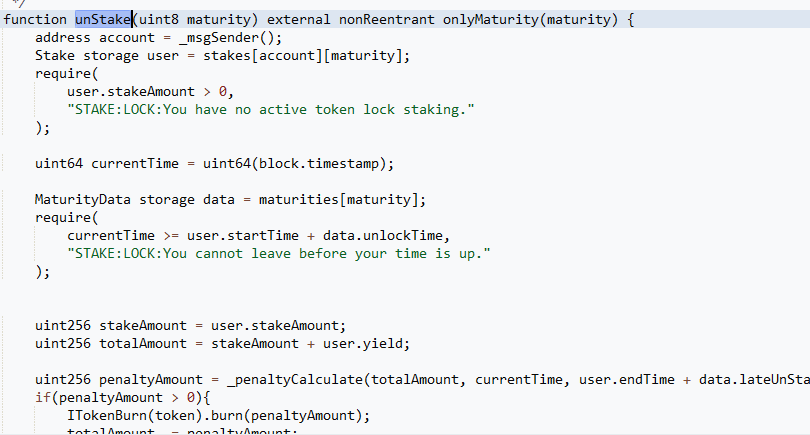
In “unStake” function, there’s no code for remove user staking info, this means anyone who staked some amount can unstake several times.
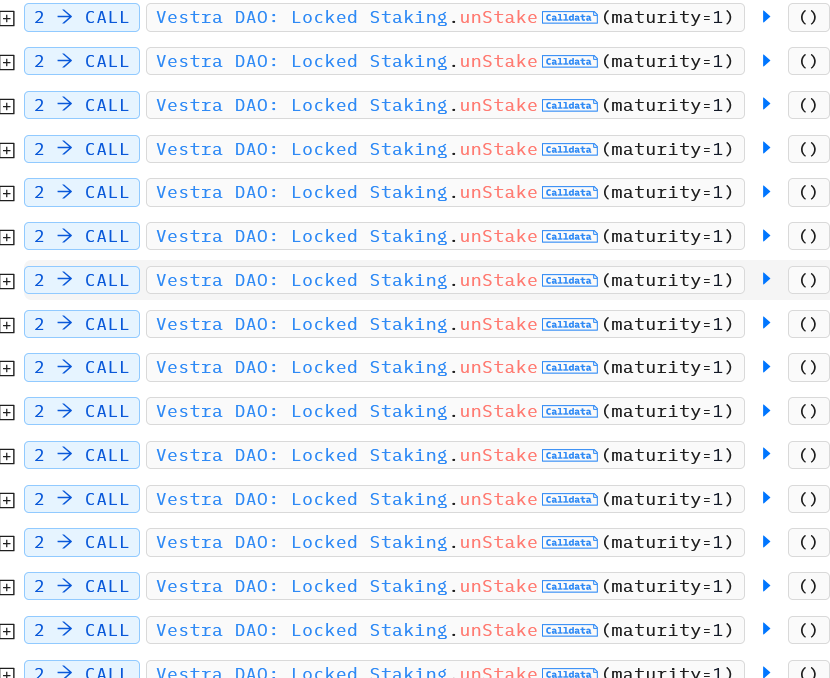
Hacker just called “unStake” several times. He prepared this attack for 1 month, because lock period is 1 month. He staked some VSTR 1 month ago, and yesterday, upgraded contract logic, then hacked.
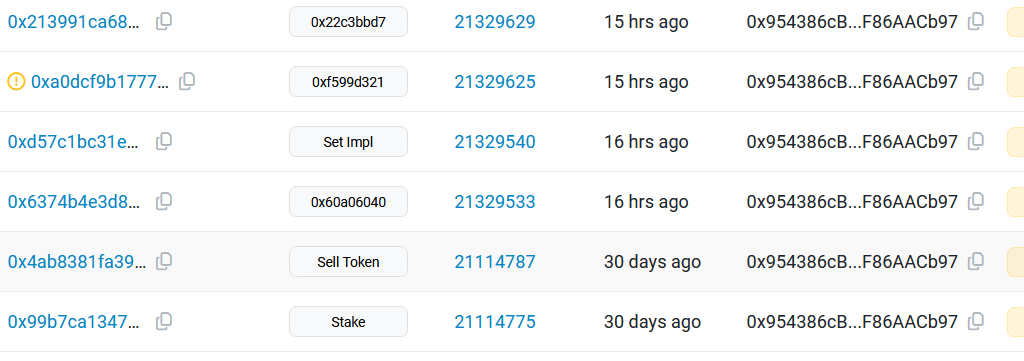
He was unable to withdraw all tokens in one tx, because of “data.totalStaked” value.
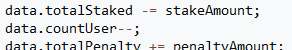
To increase this value, he created some contracts, and let them stake some VSTR tokens in next tx. Then, unstaked again.
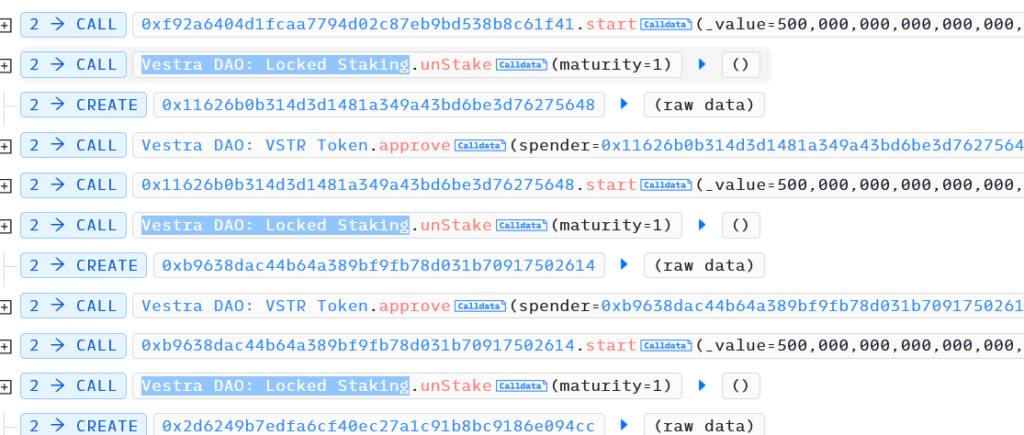
Total loss is almost $500k.
Leave a Reply