Clober Liquidity Vault was exploited, root cause is reentrance.
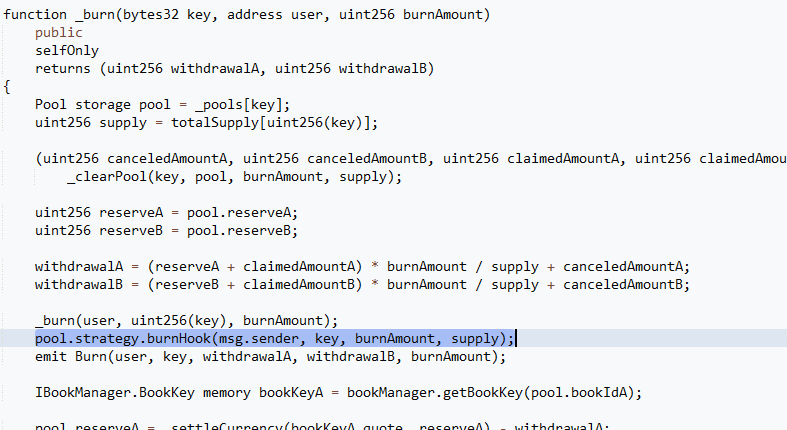
“_burn” function calls “burnHook” function of pool.strategy contract, but it has no reentrancy check.
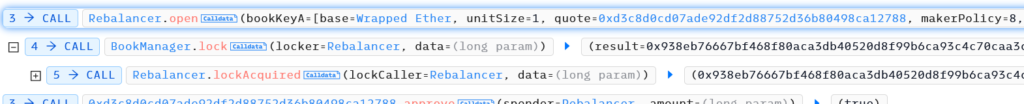
Hacker deployed his own token contract and created pool with WETH and that token using “open” function, set pool.strategy to attack contract, now “_burn” function calls “burnHook” function of attack contract.
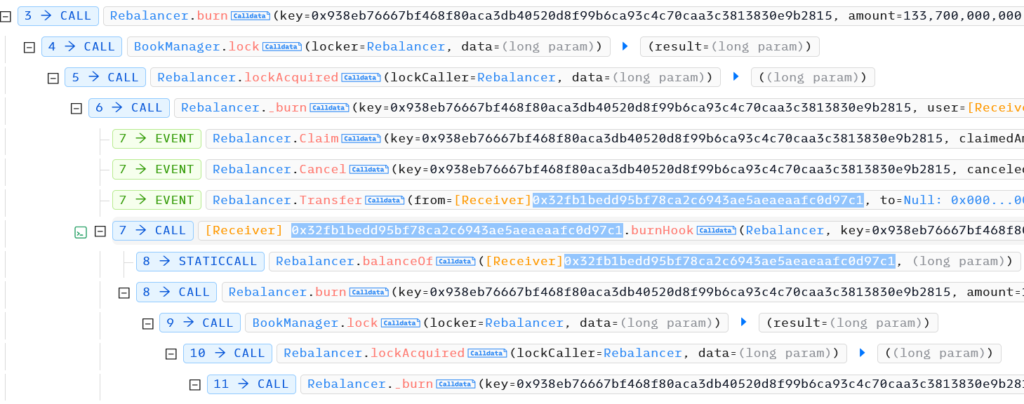
In second “burn” function, withdrawal amount was much more because reserve value was not updated.
Hacker drained all 133 WETH in vault.
Keep in mind, developers, you need to finish state update before callback function. Also, don’t forget reentrancy check.
Leave a Reply