A contract named “FortuneWheel” was exploited due to public swap functionality.
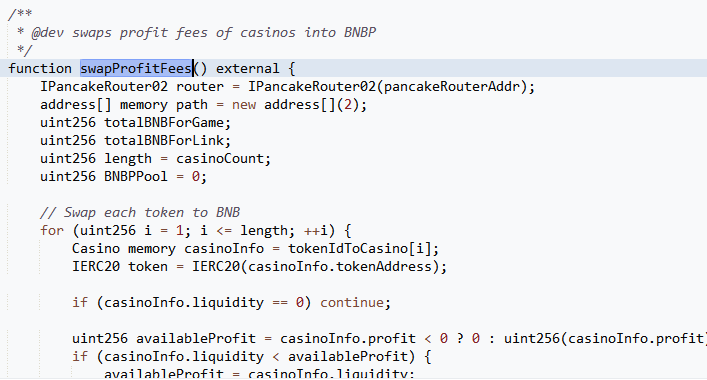
“swapProfitFees” function exchanges tokens using pancakeswap and has no modifier.
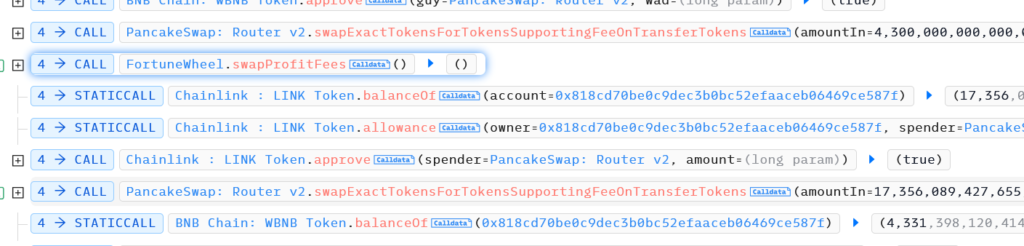
Hacker exchanged a huge amount of WBNB to LINK, then called this function, exchanged LINK to WBNB again. He gained almost $21k.
There should be access check in “swapProfitFees” function.
Leave a Reply