OdosLimitOrderRouter contract was exploited due to insufficient input check. Interestingly, function for validating signature used for call injection.
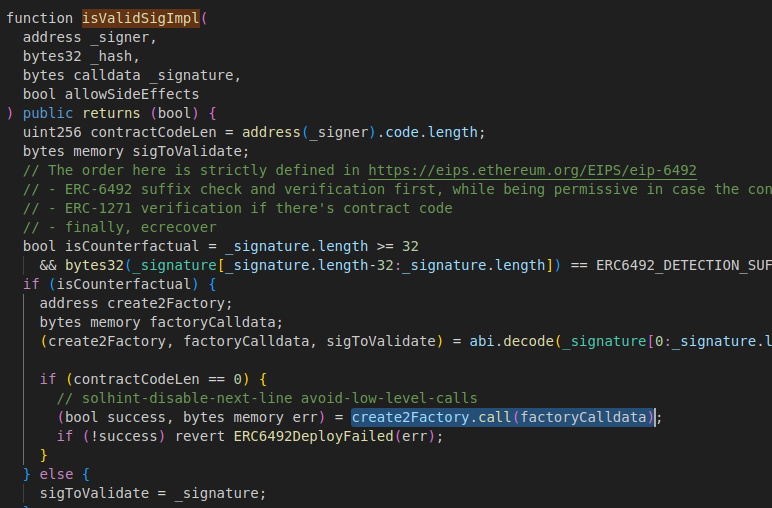
“isValidSigImpl” function parses factory address and calldata and makes an external call using parsed data, this is used for call injection.
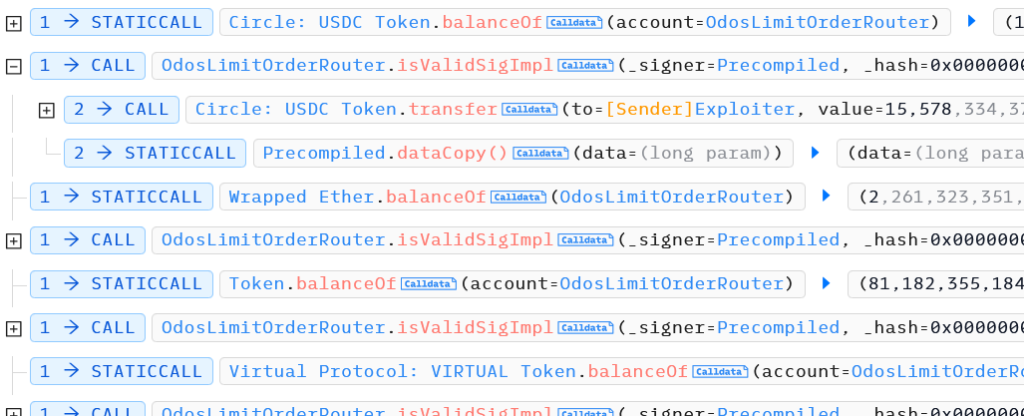
Hacker provided token contract address and calldata for “transfer” as input of “isValidSigImpl” function, all tokens in router contract were drained.
Contracts on Ethereum and Base were attacked.
Leave a Reply