An unverified contract on Base was exploited, root cause is improper input check.
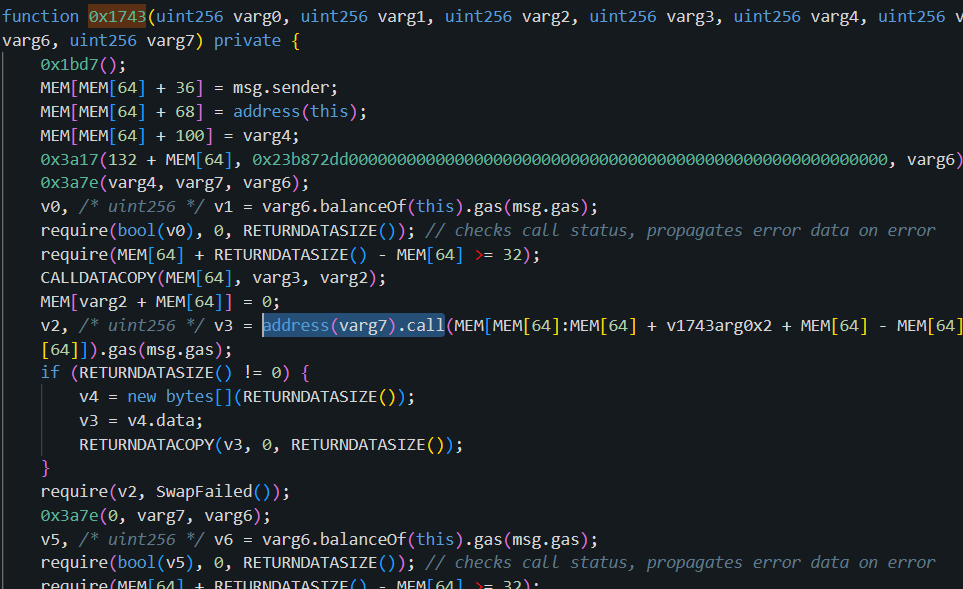
It seems that this function is used for token exchange, but as there’s no check about input for external call, this can be used for call injection.
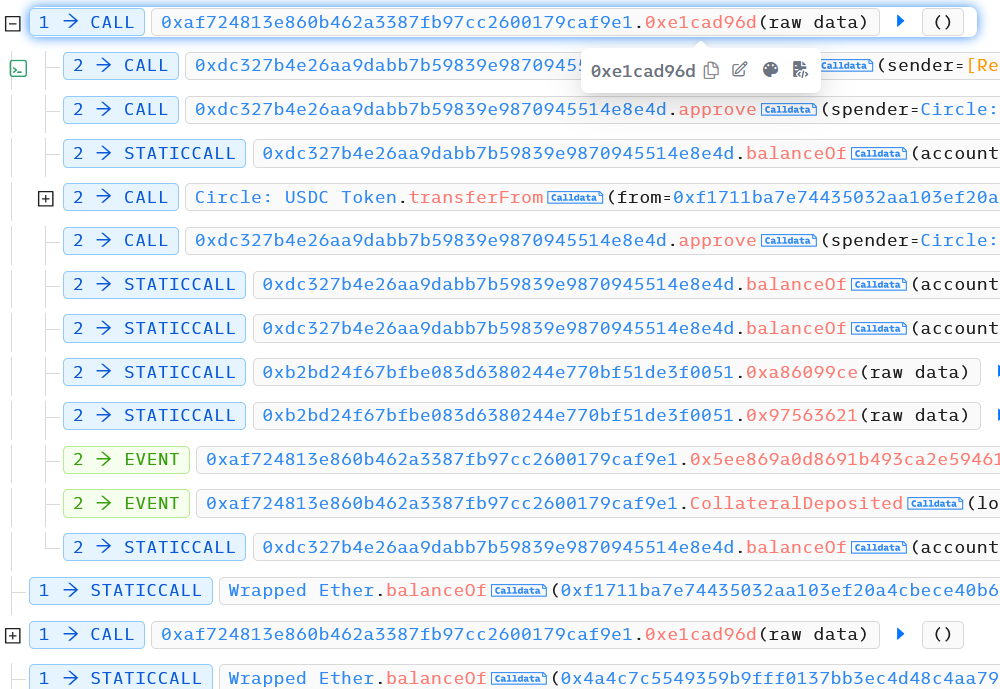
Hacker took fund from users who approved to this contract, gained $125k.
Leave a Reply